Principle of least privilege examples & best practices
The principle of least privilege access is a software security best practice that provides a user only the minimum set of rights required to perform an assigned job or function.
This principle sounds very technical, but we see examples of least privileged access everywhere in our daily lives.
List of least privilege examples
Here’s a list of some principle of least privilege examples we will look at here:
- A customer can walk through a store but not got to the shipping area
- Truckers can access the shipping area and the store but not open a cash register
- A cashier can walk through the store and open a cash register, but not go to the shipping area
- In Linux, when you create a file, you are given read and write permission, but not execute
- Users who access a public website can read files from the server but can’t edit or upload files
Everyday examples of the least privilege principle
Customers walk into a Walmart and know they have permission to grab a shopping cart, walk down the aisles and eventually approach the check-out counter. However, they are not allowed to open up a cash register or enter the shipping docks. Customers are granted access only to those things that enable to shop at the store.
A truck driver on the other hand, likely has all the rights of a customer, plus additional privileges that allow access to the shipping and receiving area.
A cashier has rights to open a register and handle cash — which a customer or a truck driver would never be allowed to do — because it’s required for them to do their job. At the same time, the cashier might not be allowed access to the shipping department.
Least privileged access applied
The principle of least privilege also underpins the world of software development. Let’s take a look at three examples where it applies to security in a software-based environment.
Least privilege in Linux: Create a file
When a Linux user creates a new file in a new folder within their home directory, the operating system only grants the user read and write access.
Least privilege in Linux: Run a script
To run a script on Linux, even if you created that script yourself, you must take extra steps to assign execute rights to the file. Linux protects the computer from viruses and malware by assigning the least amount of privileges it assumes you require to work with the files you create. If you need more than read-write access to the files you create in Linux, you must perform explicit steps to obtain those privileges.
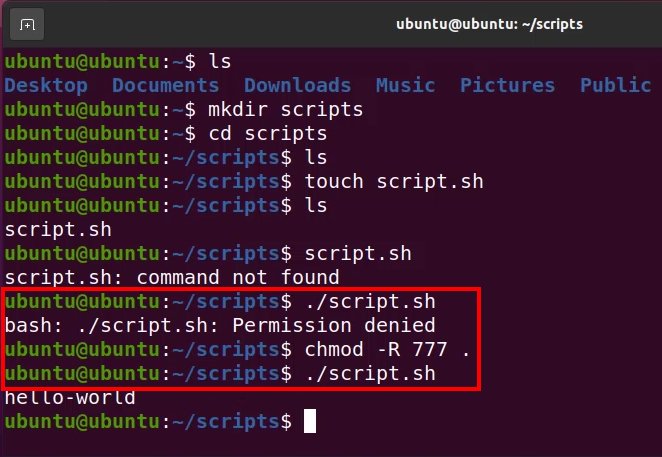
By default, Ubuntu will not allow a user to run scripts they create themselves unless new permissions are assigned.
Least privilege in AWS: Configure an S3 bucket
Cloud vendors such as IBM, Google and Azure enforce least privileged access with great diligence.
For example, when you create an S3 bucket in AWS, Amazon requires you to check a number of boxes and explicitly configure a policy that allows the S3 bucket’s content to be publicly available. Even when you jump through all the Amazon S3 hoops, AWS encourages you to provide the most minimal rights users need to access the content.
Amazon encourages HTTP GET permissions for S3 bucket content, and highly discourages POST, PUT and DELETE permissions. Those rights are not needed for users to view a website hosted on S3, or download a PDF or a spreadsheet.
Ways that the principle of least privilege applies to security of IT resources.
Least privilege access best practices
A web server such as the Apache HTTP Server or Nginx represent complex examples of the principle of least privilege.
The software itself is installed by an administrative super-user with like root-like privileges. That user is the only individual will full control over all of the files and folder associated with the installation.
Web developers never need to manipulate the web server’s installation files, but they add and update the files the web server hosts. So, assign to members of the web developer group only read and write access to the folder in the web server installation that hosts all of the files associated with the website.
Finally, assign anonymous users read access to the folder on the server that hosts the website’s files — lest nobody can visit the site. That is the absolute highest set of rights assigned to anonymous users, because that’s the least amount of privilege they need to view the site in a browser and download hosted files.
The highest priority of every DevOps professional is to implement secure systems. When assigning permissions to users, groups and resources, remember these principles of least access examples, and give users no more rights than they need to perform their task successfully.
 Cameron McKenzie is an AWS Certified AI Practitioner, Machine Learning Engineer, Solutions Architect and author of many popular books in the software development and Cloud Computing space. His growing YouTube channel training devs in Java, Spring, AI and ML has well over 30,000 subscribers.
Cameron McKenzie is an AWS Certified AI Practitioner, Machine Learning Engineer, Solutions Architect and author of many popular books in the software development and Cloud Computing space. His growing YouTube channel training devs in Java, Spring, AI and ML has well over 30,000 subscribers.



