Top 5 AWS root account best practices
Five Best practices for AWS root accounts
Keeping your Amazon account secure is a major concern for every AWS user and admin. Here are the top five AWS root user account best practices every organization should follow:
- Never share AWS root account credentials
- Delete any and all of root’s programmatic access keys
- Enable multi-factor authentication (MFA) on the root account
- Update the AWS password policy to rotate credentials every 90 days
- Perform all administrative functions with non-root accounts
Let’s break these down one by one.
AWS root account security
Credentials for the AWS root account should be shared only with a select group of individuals on the IT team. Don’t share the AWS root account with the CEO, or with an auditor or compliance officer. Only as small number of individuals should know where the root credentials are stored. Create rules about how to access that credential, and what steps to follow when the root account password is updated.
If you must assign elevated rights to a user temporarily, create a time-boxed role for that individual. But never share AWS root account credentials.
AWS root access keys
Another AWS root account best practice is to delete any programmatic access keys associated with the root user. If a PEM file or DER certificate exists for the root account, that doubles the root account’s attack surface. Delete those keys immediately.
In rare instances, an administrator might perform an administrative function as a root user. There are no reasons why a piece of software should programmatically log in as root with user’s access keys.
Enable root MFA
By default, AWS accounts are only protected by a username and password. The best practice here is to enable MFA.
With a password, you prove who you are with a piece of information that only you know. MFA ups the ante by requiring not only what you know but also what you have. In addition to a password the user must also provide a token or code, generated on a device that is not the device on which the user is attempting to log in as the AWS root.
Many Gmail or Facebook users are familiar with using SMS messages with MFA. AWS is much stricter — an SMS message to a mobile device is not a valid MFA option. For AWS, the only valid MFA options are:
- A virtual MFA device
- Universal 2nd factor security key
- Hardware MFA key fob
- Hardware display card
- GovCloud approved MFA device
Securing access to the root AWS account is a crucial best practice. If your organization uses any of the devices listed above, include them in an MFA routine.
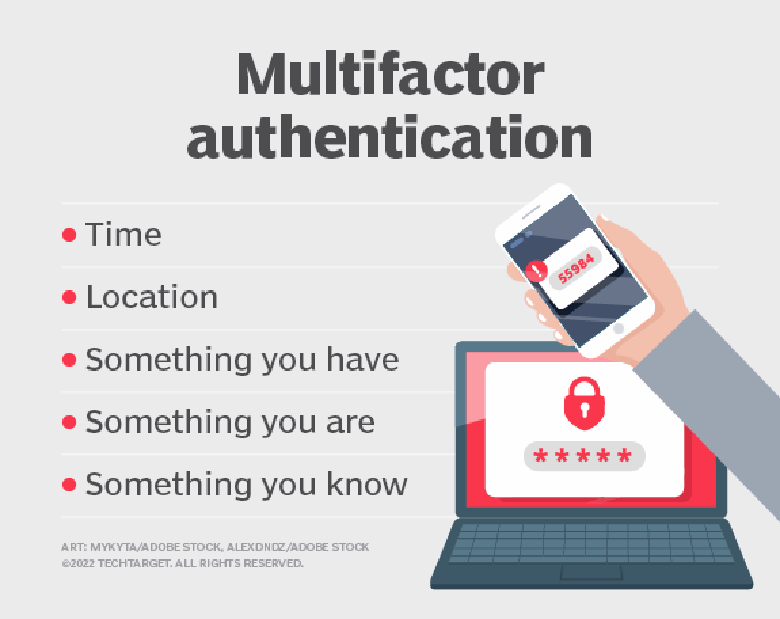
MFA is a commonly accepted best practice for root AWS account security.
Rotate AWS passwords
There is no default password rotation for the AWS root account. Once the AWS root password is set, there are no rules that require regular password updates.
However, admins can easily create a setup to regularly rotate passwords by updating the password policy attached to the account.
A general AWS root user best practice is to set the password rotation period to at least 90 days. For even more security, set it to 60 days.
Create administrative accounts
For day-to-day administration of the AWS console, create an administrative group and add trusted users who need elevated rights.
The root AWS account can never be deleted, and the rights associated with the root account cannot be revoked. Admins can, however, remove a user from the administrative group or suspend a user’s account altogether.
Furthermore, with administrative access provisioned on a per-account basis, admins can monitor the actions of a specific user to identify any peculiar activity that warrant investigation. If the root account is shared by multiple users, there is no way to identify which user performed which administrative tasks.
More AWS security best practices
A core tenet of server-side security is to respect the principle of least privilege.
An AWS root account best practice is to always respect the principle of least privilege.
How to protect the super user account
An admin should assign to users only the minimal rights to perform their required tasks. Furthermore, don’t add users to the administrative group every time they perform a one-off administrative function — use AWS roles instead.
Also, regularly monitor exactly who is included in your account’s administrative group. If a user moves on to a non-administrative role, do not allow that user to perform management functions in AWS.
Follow these AWS root account best practices, and you’ll ensure that nefarious cyber-criminals never gain access to your cloud-computing credentials.



